Quantum Key Distribution Ultimate Security for Modern Network Key Exchanges

QKD: The Ultimate Triumph of Cryptography
Quantum Key Distribution (QKD) is poised to revolutionize the world of encryption key exchange, marking the end of the age-old battle between codemakers and codebreakers. Unlike all previous key exchange methods, QKD is absolutely unbreakable, thanks to the fundamental laws of quantum physics.
In traditional cryptography, codemakers rely on complex mathematical algorithms to create codes that are difficult or impossible for codebreakers to decipher. However, even the most sophisticated traditional encryption algorithms are vulnerable to attack by increasingly powerful computers.
QKD, on the other hand, exploits the unique properties of quantum mechanics to create the mechanism that is truly unbreakable. In QKD, the parties exchange photons, which are particles of light. These photons are in a superposition of different quantum states.
If an eavesdropper tries to intercept the photons during the exchange, they will inevitably disturb the superposition, which will alert the codemakers and codebreakers. This makes QKD completely immune to eavesdropping.
QKD protocols are generally classified into two broad categories:
Prepare-and-Measure Protocols: In these protocols, the sender prepares a quantum state (often as a superposition of the polarization states of light) and sends it to the receiver, who then measures it. The information about the key is encoded in the quantum states prepared by the sender. If there is an interception, the superposition is disturbed, and such a disturbance can be detected by the communicating parties. The quintessential example of Prepare-and-Measure Protocols is the BB84 protocol, named after its creators Charles Bennett and Gilles Brassard, who introduced it in 1984.
Entanglement-Based Protocols: In entanglement-based protocols, a source generates entangled pairs of quantum states, and each party receives one member of the pair. Both parties perform measurements on their respective parts. The shared key is created thanks to the quantum entanglement of the members of the pair. If there is an attempt at interception, then, due to the quantum no-cloning theorem, an eavesdropper cannot simply copy the entangled particle to gain information without being detected. The E91 protocol, proposed by Artur Ekert in 1991, is an example of an entanglement-based protocol.

In another classification, we divide existing QKD systems into:
Discrete Variable (DV) QKD Protocols: These involve the use of quantum systems with discrete energy levels to encode information. These protocols typically use single photons as the carriers of information, and the key bits are encoded in specific properties of these photons, such as their polarization, phase, or time-bin. The BB84 protocol is a prime example of this category. However, the E91 protocol should not be classified here as it is an entanglement-based protocol, which, while it also uses discrete variables (like polarization), relies on the quantum correlation of entangled photon pairs rather than the properties of individual photons.
Continuous Variable (CV) QKD Protocols use quantum systems with continuous spectra to encode information. CV-QKD protocols typically use the quadratures of the electromagnetic field, which are analogous to the position and momentum of a quantum particle. They can take on any value within a continuous range, hence the name “continuous variable.” The security of CV-QKD is based on the uncertainty principle which ensures that certain pairs of physical properties cannot both be measured with arbitrary precision at the same time. An eavesdropper attempting to measure the transmitted quantum states will introduce noise, which can be detected by the communicating parties. Protocols that use Gaussian-modulated coherent states are examples of this category.
We offer both families of QKD systems in our portfolio.
A True Perspective on QKD
Let’s clear up a common misconception about Quantum Key Distribution (QKD) technology. While it indeed represents a significant advancement in cryptographic security, it’s important to understand that QKD does not encrypt data.
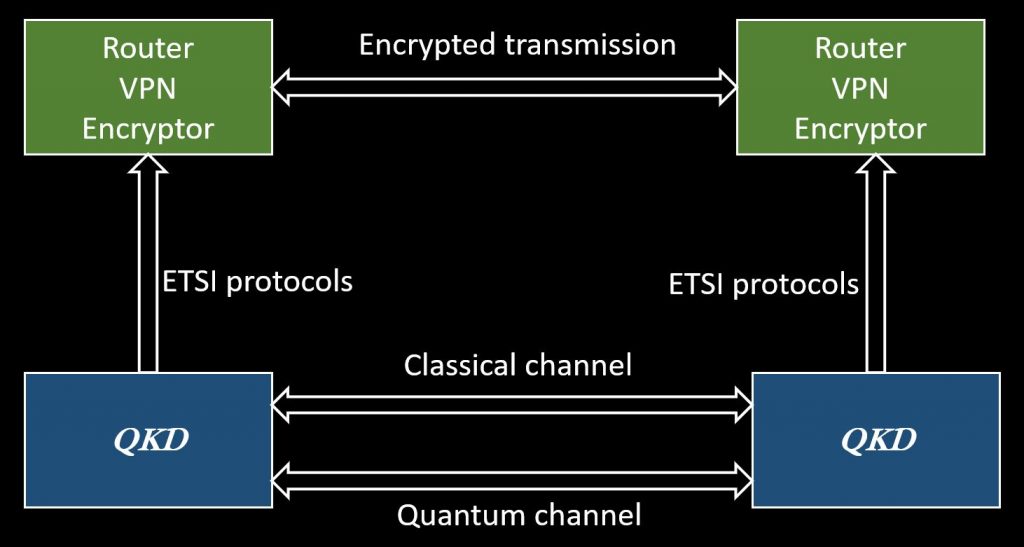
Instead, QKD serves one, absolutely fundamental role in digital security: ensuring the secure exchange of encryption keys between a sender and a receiver. As illustrated in the accompanying diagram, QKD NEVER operates in isolation—it is part of a larger security infrastructure that includes encryptors, VPN systems, or other mechanisms that perform the actual encryption.
This approach aligns with long-established and proven principles, such as those articulated by Auguste Kerckhoffs, and the theoretically secure methods developed by Claude Shannon.
Our extensive knowledge and practical experience (also related to our pQKD devices and QCMS services) enable us to recommend the most suitable encryption solutions. These range from basic optical (Layer 1) to advanced systems, adapt your VPN setup for quantum security, and configure your organization’s entire security ecosystem to be prepared for Y2Q (Year to Quantum).
We partner with premier QKD innovators and suppliers:
QNU Labs: India’s forefront in quantum-safe communications, QNU Labs crafts QKD systems that fortify data against formidable threats, catering to government and high-stakes industries.
Quintessence Labs: Pioneering in Australia, Quintessence Labs offers a quantum-resilient shield for information via advanced key generation, agile management, and QKD—preparing organizations for a secure quantum era.
QuantLR: From Israel, QuantLR delivers cost-effective quantum cryptography, harnessing quantum mechanics to future-proof data security in the face of emerging quantum challenges.
We sell, maintain, and provide full support for all products from these three leading companies.

If you're interested in purchasing QKD systems, require assistance with implementation and integration, or would like to receive more information about our services, please fill out the form below:
Place Your Order
Thank You for Your Order!
Your order has been successfully placed. We'll send you a confirmation email shortly.
Order Reference:
